WordPress plugins enhance functionality, but they can also introduce security risks if not managed properly.
WordPress plugins can become security risks due to:
- Outdated or abandoned plugins
- Poorly coded plugins with security flaws
- Exploited vulnerabilities in widely used plugins
- Malware-infected plugins from untrusted sources
In 2024, there were 8,000 WordPress vulnerabilities reported and a huge 96% of the flaws were found in plugins.
This guide will help you understand the best practices to secure your WordPress website.
Best Practices to Protect Your WordPress Site
1. Keep Plugins Updated
Regularly update all installed plugins to ensure you have the latest security patches. Outdated plugins leave a big security threat for your website.
In December 2024, an arbitrary file upload vulnerability was identified in the Chaty Pro plugin, affecting approximately 18,000 WordPress sites. This allowed attackers to upload malicious files to the server, potentially leading to remote code execution and full site compromise.
A fix was released in February 2025 (3 months after the flaw was found), however, because many website owners delay updating their plugins, attackers can take advantage of this by using scanning tools to identify which websites are still running old versions.
To combat against this, enable automatic updates where possible and review changelogs before updating. It’s also advisable to set a schedule to check for plugin updates.
With My20i, you can review all the installed plugins on your WordPress website using the WordPress Manager , which will show any plugin that needs to be updated.
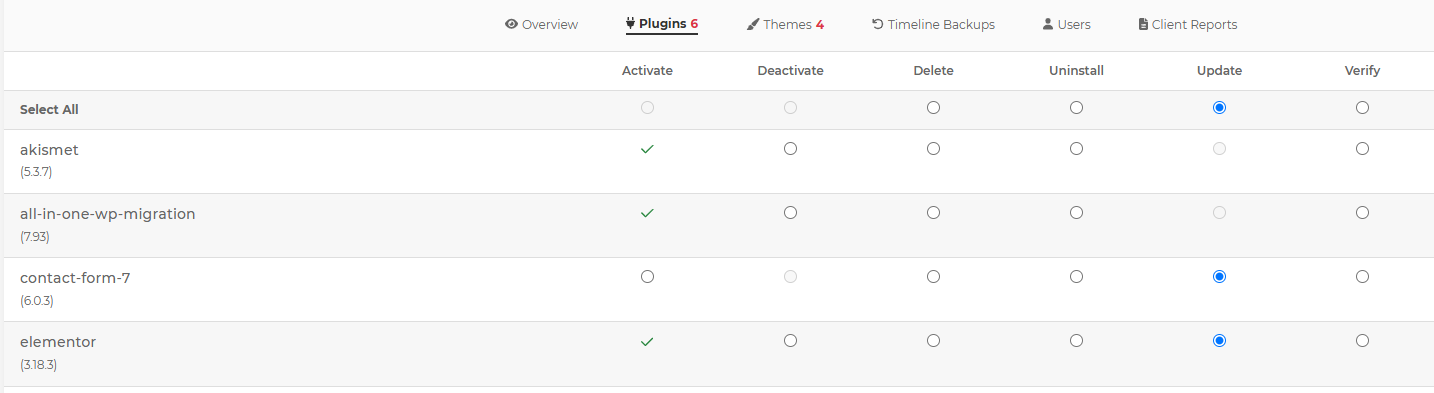
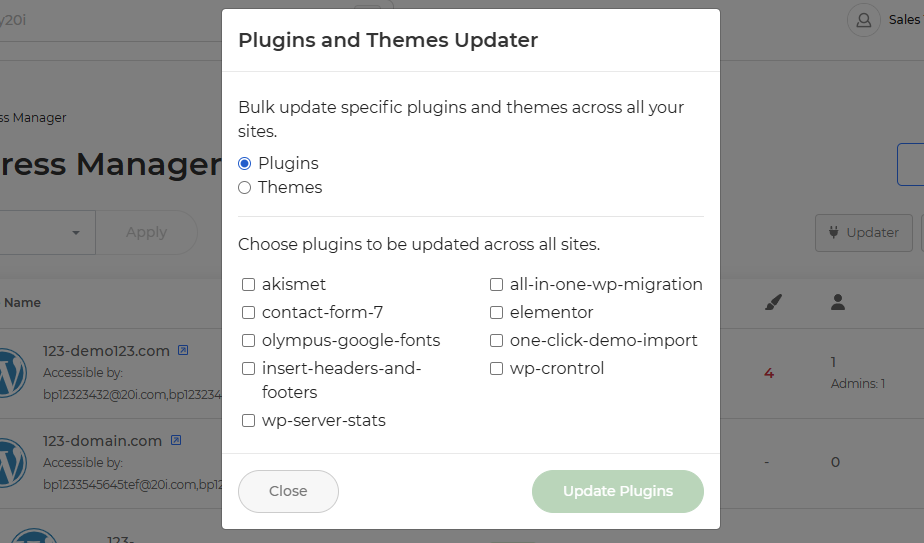
You can also use this to run bulk plugin updates across your websites and you can select specific plugins to be updated, giving you more control.
2. Only Use Trusted Plugins

Download plugins from reputable sources such as the WordPress Plugin Repository or well-known premium developers.
Avoid nulled plugins or plugins coming from unknown sources, as these could contain badly written code or even malware.
To ensure that you have found a good plugin, you can usually find reviews on the plugin itself. Make sure the plugin developers have a proven track record of being trustworthy.
On WordPress.org you can see how many active installations there are, and you can stay informed about security risks by using trusted databases such as WPSCan for any known vulnerabilities.
3. Limit Plugin Installations

Only install plugins that are essential for your site. More plugins increase the attack surface and potential vulnerabilities.
If a plugin has security flaws, such as outdated code or is no longer maintained by its developers, it increases the likelihood of your website becoming malware infected.
You can reduce risks by:
- Only use well-coded, reputable plugins from trusted sources, such as the official WordPress repository.
- Regularly update your plugins to ensure you’re protected against newly discovered vulnerabilities.
- Remove unused or inactive plugins to reduce security risks and declutter your site.
- Consider built-in or native solutions. With our WordPress optimised hosting, we already offer WordPress staging, Cloning, Web optimisation tools, CDN, Bespoke Cache plugin, plugin and theme management tools. Because these tools are on the server level, this also saves on PHP bloat for your website.
4. Implement a Web Application Firewall (WAF)

At 20i, we include a WAF at no extra charge. The protection takes place at the edge of our network, inspecting every request for SQL injection, trojans, cross-site scripting, path traversal and many other types of attack and protecting against them before the request reaches your websites code.
Comparable Security plugins with premium features, like Securi or WordFence come at an additional cost, over $230 per year.
5. Check your website for malware and monitor suspicious activity

Security plugins like Wordfence, MalCare, or iThemes Security scan for malware, and suspicious activity.
At 20i, we scan your websites every day for Malware and if malware is detected we’ll send you an email with a report with the exact location of where the malware was found and you can access your websites files via the file manager or FTP to remove the malicious code. You can also run a malware scan on demand.
We monitor every HTTP request made to our system, as well as requests from IP addresses we’ve classified as ‘suspicious.’
These are typically IP addresses we’ve previously identified as being associated with fraudulent or suspicious activity.
Our StackProtect system automatically blocks requests from these IP addresses to help prevent any potential threats.
6. Use Least Privilege Access Control

Apply the principle of least privilege when assigning user roles in WordPress. Only give users the minimum permissions necessary to perform their tasks.
For example, contributors shouldn’t have access to install or update plugins, and only trusted admins should have full access to the site’s backend.
This reduces the potential damage in case an account is compromised, or a user makes a mistake. Use role management plugins like User Role Editor if you need more granular control.
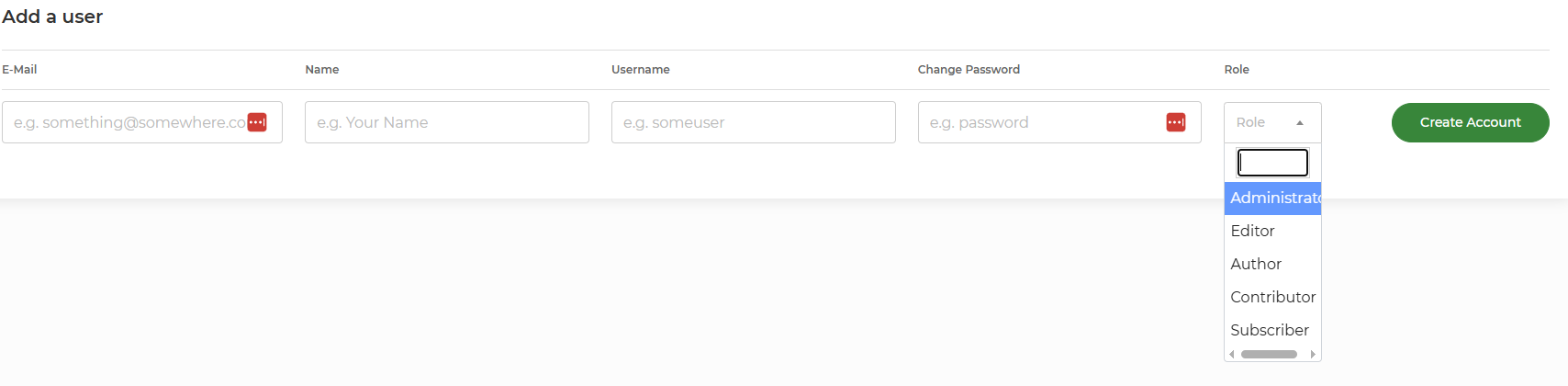
You can also assign a user role using our WordPress toolset when creating WordPress users.
7. Monitor Vulnerabilities and Threat Feeds
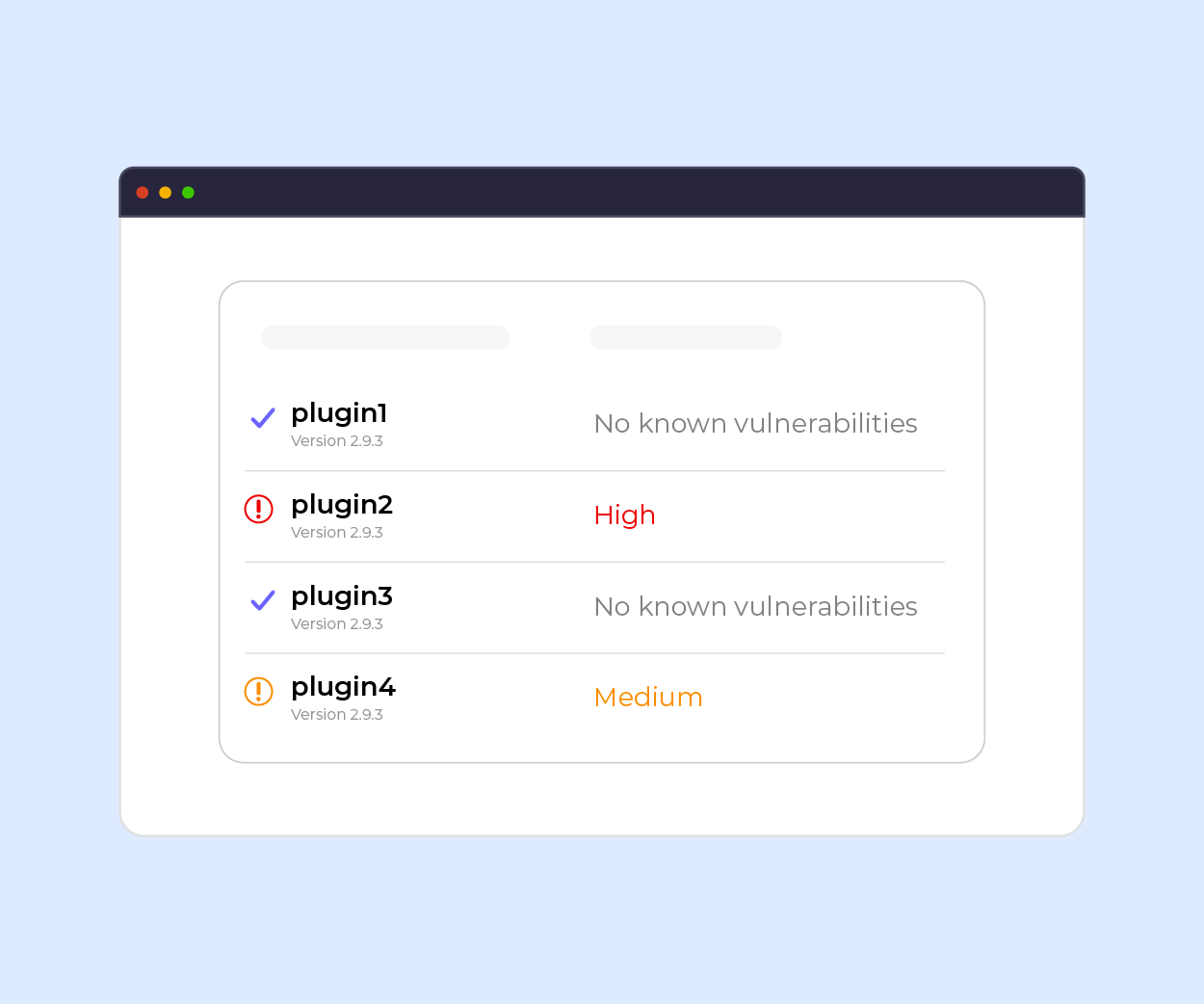
To stay ahead of threats, you can follow trusted sources like WPScan Vulnerability Database a highly comprehensive and a well-maintained database for WordPress-related security issues. It tracks known vulnerabilities in WordPress core, themes, and plugins.
Also Exploit Database, this is managed by Offensive Security. The platform publishes proofs of concept for exploits across a wide range of technologies including WordPress plugins. It’s more technical but can help you identify high risk plugins before they become an issue.
8. Regular Backups

As WordPress websites can be vulnerable to threats such as outdated plugin, themes and core versions, it’s important to take regular backups of your website and database so you can quickly recover the website data in the event of a malware attack. If you have access to the website files and database, you can usually download copies using FTP and phpMyadmin.
At 20i, you can create manual backups anytime using our Backup/Restore tool. Free daily automated backups are included with Managed Cloud Hosting and Autoscale Hosting, while automated backups can also be added as an optional extra on Reseller Hosting plans.
9. Choose a Secure Hosting Provider – like 20i!
Choosing a hosting provider that offers built-in security will help you stay protected from malware, hacking attempts, and downtime caused by malicious traffic.
At 20i, we take security seriously and provide enterprise level security across all our hosting plans.
In addition to Anti DDOS Protection, Brute Force protection, Web Application Firewall and Malware scanner, we also include additional advanced security measures such as:
- External access to databases is disabled by default (you can allow IP addresses access via My20i)
- SSH access requires a public and private key pair or 2FA
- Free SSL certificates to ensure transmission over the web is secure
- ISO-270001 accredited data centres with 24 hour manned security
- Separated process execution and file ownership
Conclusion
While plugins offer enhanced functionality, they’re also a common source of security vulnerabilities.
Taking a proactive approach to your website security i.e. limit plugin installations, choosing trusted sources and regularly updating plugins will help reduce security risks.







Add comment