Introduction
Phishing is one of the most pervasive and effective forms of cybercrime. It involves fraudulent attempts to trick individuals into revealing sensitive information such as passwords, credit card numbers or login credentials, by impersonating trusted entities.
This is often conducted via email, but it can also occur through websites, text messages, or voice calls.
Once they gain access, attackers can then move laterally within a network and attempt to escalate privileges, paving the way for a much larger cyber-attack.
This article examines the various types of phishing, highlighting the role of email spoofing, and provides strategies for you to defend against these threats.
What Is Phishing?
Phishing is a social engineering attack that aims to exploit human trust rather than technical vulnerabilities in a system. It takes advantage of a user’s willingness to follow instructions from what appears to be a legitimate source, such as a bank, service provider or employer.
Typical attacks use methods such as…
- Urgent action required e.g., “Click here or your account will be suspended” or “You’re a winner, click here to claim your prize”
- Malicious links or attachments, used to infect the user’s device with malware.
- Cloning reputable brands’ email templates to capture sensitive data or login credentials that will later be used to defraud the target, steal further information, steal money or intellectual property.
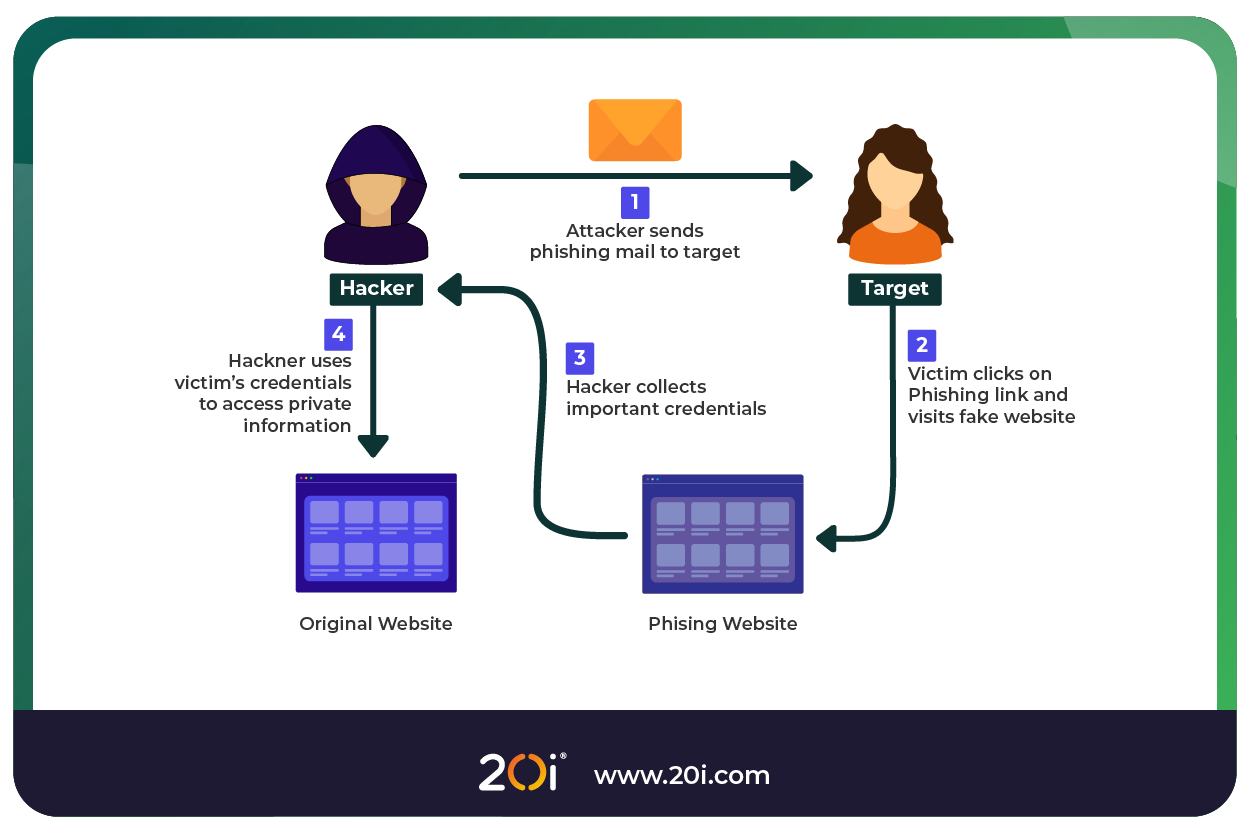
Email Spoofing and Its Role in Phishing
Email spoofing is a common technique used to impersonate a legitimate sender. The attacker manipulates the email “From” address to make it appear as if the message comes from a trusted individual or domain.
By combining spoofed sender information with legitimate branding and language, attackers increase the chances that victims will click links or open malicious attachments.
Here’s an example of phishing via email spoofing:
- An email appears to come from support@yourbank.com but actually originates from a malicious IP address and includes a link to a fake login page.
- The user inputs their details
- Once the victim enters their details, these are then sent to the malicious actor, who can then access the victim’s account on the legitimate website.
Phishing Vs. Pharming
Pharming is a type of cyberattack that redirects users from legitimate websites to fraudulent ones without their knowledge.
Unlike phishing, which typically relies on tricking individuals into clicking a malicious link, pharming manipulates the underlying infrastructure of the internet.
This can be done in two main ways:
DNS poisoning (DNS spoofing)
The attacker corrupts the Domain Name System (DNS) cache or server, so that when a user types in a legitimate web address, they’re unknowingly redirected to a fake site controlled by the attacker.
Local host file modification:
The attacker alters the local host file on the victim’s computer, which maps domain names to IP addresses. This bypasses DNS and redirects traffic to a fake site even if the correct web address is entered. This is usually achieved through social engineering or malware.
Types of Phishing Attacks
Email Phishing (Mass Campaigns)
Much like marketing campaigns, phishing campaigns are sent to thousands of recipients and commonly attempt to spoof large brand names like Microsoft, Amazon, PayPal, etc.
The goal of this is to collect credentials for the respective websites or infect systems with malware.
Spear Phishing
Sper phishing is a highly targeted and personalised variation of a traditional phishing attack. These are aimed at specific individuals or roles within a company and the attacker. Often uses detailed knowledge of the victim or organisation to boost credibility.
Usually, the attacker will gain intelligence of their target, such as names and hierarchy and will exploit this knowledge to pose as a legitimate, known actor.
Business Email Compromise
Spoofs mail to originate from executives or partners to manipulate employees into making payments or disclosing sensitive data. Often coupled with urgency, this involves email spoofing and social engineering to fool subordinates into disclosing sensitive information.
Smishing (SMS/text message Phishing)
Smishing is delivered via text message or SMS (Short Message Service) and may include malicious links or fake account notifications. Malicious actors often impersonate banks, delivery services, and government agencies to steal sensitive information.
Vishing (Voice Phishing)
Attackers call victims pretending to be support agents, IT staff, or government officials to extract information or persuade the target to perform an action such as install malicious software or disclose sensitive information.
Clone Phishing
Clone phishing is the act of copying a legitimate email, changing the links or attachments, and resending it. As the victims will likely have seen similar emails before, this exploits familiarity to increase trust.
Common Phishing Tactics
Urgency and fear
The most common phishing tactic is using urgency to instil fear into their victims. This could be claiming that a payment for a large sum of money is due to leave their account and to contact them (the attacker) if the victim didn’t action this. The attacker will then gather sensitive information from the victim to further exploit their trust.
This method is particularly effective, as it causes the victim to act fast, often causing them to overlook discrepancies differentiating the attacker from the legitimate source.
Spoofed email addresses/domains
Spoofing email addresses and domains is a very effective way for an attacker to pose as a legitimate source. As this involves them sending emails from a legitimate domain, it is much harder to detect.
This attack is not very effective at posing as large firms, such as Google or Apple, as these companies will have security measures, such as SPF, DKIM and DMARC in place to prevent their domains from being spoofed.
Phishing websites
An attacker can create an exact clone of an existing website and will often attempt to use a domain as similar to the legitimate source as possible, such as ‘bar.clays-bank.com’.
This method is often paired with email spoofing, smishing, vishing etc to boost its footfall and attempts to trick victims into entering their credentials, which are then harvested.
Malicious attachments
Malware can be sent to victims via phishing and is often disguised as invoices, resumes, or security reports. When the victim downloads the malicious attachment, malware will be installed on their device which will be used to harvest credentials, gather personal data and potentially extort the victim.
Most email providers, such as 20i, can automatically detect malware in attachments and outright reject the email or display a warning for the recipient.
How to Prevent Phishing Attacks
At 20i, we don’t believe that you should have to pay extra for security features, so we include an extensive security suite with our Reseller, Autoscale and Managed Cloud Hosting services.
As a reseller, this is something that you can advertise as your own and provide to your customers for free to distinguish yourself from mediocre hosting providers.
Implement Email Authentication
Use SPF, DKIM, and DMARC to prevent bad actors from impersonating your brand.
A Sender Policy Framework (SPF) record is a DNS TXT record that helps prevent email spoofing and the record is automatically added to the DNS on our platform.
When an email is received, the recipient’s mail server will check the SPF record of the sender’s domain to verify whether the sending mail server is permitted to send emails on behalf of that domain.
The purpose of DomainKeys Identified Mail (DKIM) is to authenticate that the content of any DKIM-signed email message is not modified during the transfer between sender’s or ISP (Internet Service Provider) and receiver’s mail servers.
Domain-based Message Authentication, Reporting, and Conformance (DMARC) works in conjunction with SPF and DKIM records and is designed to prevent the domain from being spoofed.
Use Advanced Email Security Solutions
Many modern mail providers will have security measures in place to minimise the risk of you receiving phishing scams. At 20i, we use three layers of security on our advanced Stackmail platform:
- Network-level – we utilise multiple deny lists from Spamhaus, Invaluement and Barracuda Networks to block any known bad actors.
- Virus scanning – our comprehensive virus scanner will automatically scan emails and attachments for known malware signatures. This database is continuously updated to stay ahead of the curve.
- Content-based – all messages are scanned for spam and phishing-like characteristics and either sent to spam/junk or outright rejected. You can also change your own personal settings to be more lenient or strict for spam on a per mailbox basis.
Conduct Regular User Awareness Training
For companies, it is beneficial to teach employees how to spot phishing indicators, such as generic greetings (“Dear user”), spelling or grammar mistakes, and hovering over links to inspect URLs before visiting.
We also encourage companies to run phishing simulations to test and improve user response to get accurate data on how phishing incidents are handled.
Keep Software and Browsers Updated
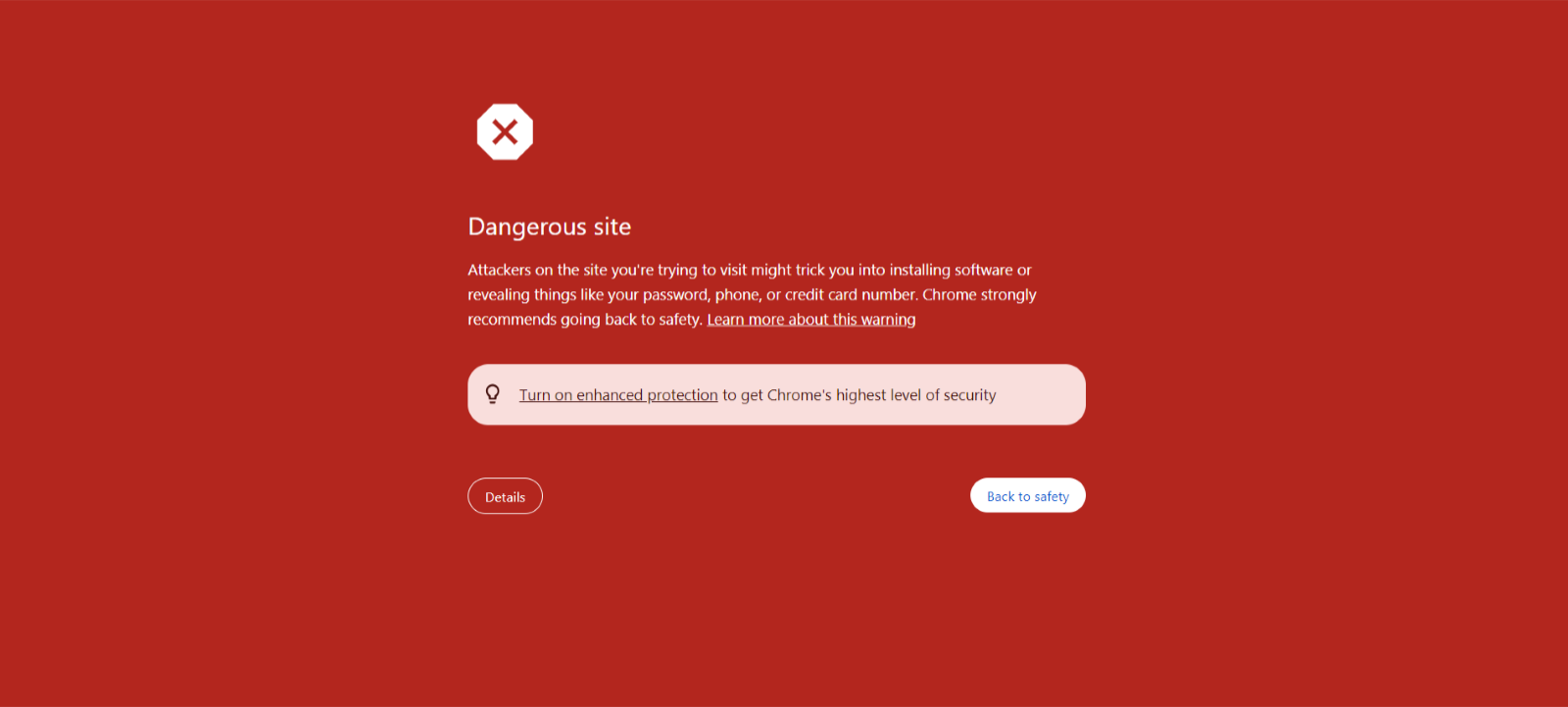
To combat phishing websites, it is advised to keep your web browsers and antivirus tools up to date as browser security features and antivirus tools can block known phishing sites and payloads.
Search engines, like Google are typically very fast to take action against a malicious website and will typically show a ‘Dangerous Site” warning as shown below.
Monitor Old Accounts
If an attacker manages to access an old, redundant mailbox, they can use this to boost credibility and other members of the same organisation are more likely to trust the attacker’s advances.
In a small team, this may be easily detected but in larger teams, especially if virtual or spread across multiple locations, this can pose a substantial risk.
Due to this, it is advised to:
- Frequently delete mailboxes that are no longer in use, particularly those of ex-employees
- Regularly check mailboxes that are rarely used
- Ensure passwords are regularly changed and are as complex and lengthy as possible
Reporting
Report phishing attempts to the relevant teams within your organisation so that word can be spread to minimise the chances of a colleague falling victim to it.
You can also report phishing scams to platforms like report@phishing.gov.uk or reportphishing@apwg.org.
Conclusion
Phishing remains one of the most effective and widespread cyber threats with tactics that continue to evolve and exploit human psychology.
Targeting individuals and businesses alike, it is imperative to ensure you and your organisation take a multi-layered approach to defence.
By combining a secure mail platform, like Stackmail, with technical safeguards, such as SPF/DKIM/DMARC and email filters with user education and vigilance, you can significantly reduce your exposure to phishing and the damage it can cause.








Add comment